Cryptography is the study and practice of techniques for secure communication in the presence of third parties called adversaries. It deals with developing and analyzing protocols which prevents malicious third parties from retrieving information being shared between two entities thereby following the various aspects of information security. In Cryptography, an Adversary is a malicious entity, which aims to retrieve precious information or data thereby undermining the principles of information security.
Data Confidentiality, Data Integrity, Authentication
and Non-repudiation are core principles of modern-day cryptography.
- Confidentiality refers
to certain rules and guidelines usually executed under confidentiality
agreements which ensure that the information is restricted to certain
people or places.
- Data
integrity refers to maintaining and
making sure that the data stays accurate and consistent over its entire
life cycle.
- Authentication is
the process of making sure that the piece of data being claimed by the
user belongs to it.
- Non-repudiation refers
to ability to make sure that a person or a party associated with a
contract or a communication cannot deny the authenticity of their
signature over their document or the sending of a message.
Cryptography is classified into symmetric
cryptography, asymmetric cryptography and hashing.
Ø Symmetric
key cryptography –
It involves usage of one secret key along with encryption and decryption
algorithms which help in securing the contents of the message. The strength of
symmetric key cryptography depends upon the number of key bits. It is
relatively faster than asymmetric key cryptography. There arises a key
distribution problem as the key has to be transferred from the sender to
receiver through a secure channel.
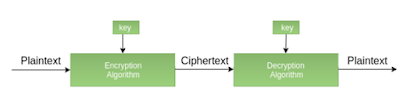
The encryption and decryption process uses the same
key. It is also called as secret key cryptography. The main
features of symmetric cryptography are as follows −
- It
is simpler and faster.
- The
two parties exchange the key in a secure way.
The major drawback of symmetric cryptography is that
if the key is leaked to the intruder, the message can be easily changed and
this is considered as a risk factor.
There are two types of symmetric encryption
algorithms:
- Block
algorithms. Set lengths of bits are
encrypted in blocks of electronic data with the use of a specific secret
key. As the data is being encrypted, the system holds the data in its
memory as it waits for complete blocks.
- Stream
algorithms. Data is encrypted as it
streams instead of being retained in the system’s memory.
Some examples of symmetric encryption algorithms
include:
- AES
(Advanced Encryption Standard)
- DES
(Data Encryption Standard)
- IDEA
(International Data Encryption Algorithm)
- Blowfish
(Drop-in replacement for DES or IDEA)
- RC4
(Rivest Cipher 4)
- RC5
(Rivest Cipher 5)
- RC6
(Rivest Cipher 6)
AES, DES, IDEA, Blowfish, RC5 and RC6 are block
ciphers. RC4 is stream cipher.
The most popular symmetric key algorithm is Data
Encryption Standard (DES).
Some examples of where symmetric cryptography is
used are:
- Payment
applications, such as card transactions where PII needs to be protected to
prevent identity theft or fraudulent charges
- Validations
to confirm that the sender of a message is who he claims to be
- Random
number generation or hashing
Ø Asymmetric key cryptography –
It is also known as public key cryptography because it involves usage of a
public key along with secret key. It solves the problem of key distribution as
both parties uses different keys for encryption/decryption. It is not feasible
to use for decrypting bulk messages as it is very slow compared to symmetric
key cryptography.
Advantages of using asymmetric encryption include:
- Key
distribution not necessary: securing key
distribution channels has long been a headache in cryptography. Asymmetric
encryption eliminates key distribution entirely. The needed
public keys are exchanged through public-key servers, and the disclosure
of public keys is not, at this time, detrimental to the security of
encrypted messages, because they cannot be used to derive private keys.
- Exchange
of private keys not necessary: with asymmetric
encryption, private keys should remain stored in a secure location and
thus private to the entities using them. Basically, the keys needed to
decrypt sensitive information are never, and should not ever be, exchanged
over a potentially compromised communication channel, and that’s a major
plus for the security and integrity of encrypted messages.
- Digital
signature/message authentication: with asymmetric
encryption, senders can use their private keys to digitally sign and
verify that a message or file originated from them and not an untrusted
third party.
Drawbacks
- Due
to its key length, it contributes lower encryption speed.
- Key
management is crucial.
Examples of asymmetric encryption
include:
- Rivest
Shamir Adleman (RSA)
- the
Digital Signature Standard (DSS), which incorporates the Digital Signature
Algorithm (DSA)
- Elliptical
Curve Cryptography (ECC)
- the
Diffie-Hellman exchange method
- TLS/SSL
protocol



No comments:
Post a Comment